Cracking Wheelio Encryption
Ever visited one of those dropshipping sites with a spinning wheel that offers coupon codes and wondered where those codes are stored? Well, I did, so I decided to dig in and figure out how it works.
Analyzing the Main Script
After downloading the main Wheelio script and deobfuscating it using restringer, I ended up with something that looked like this: 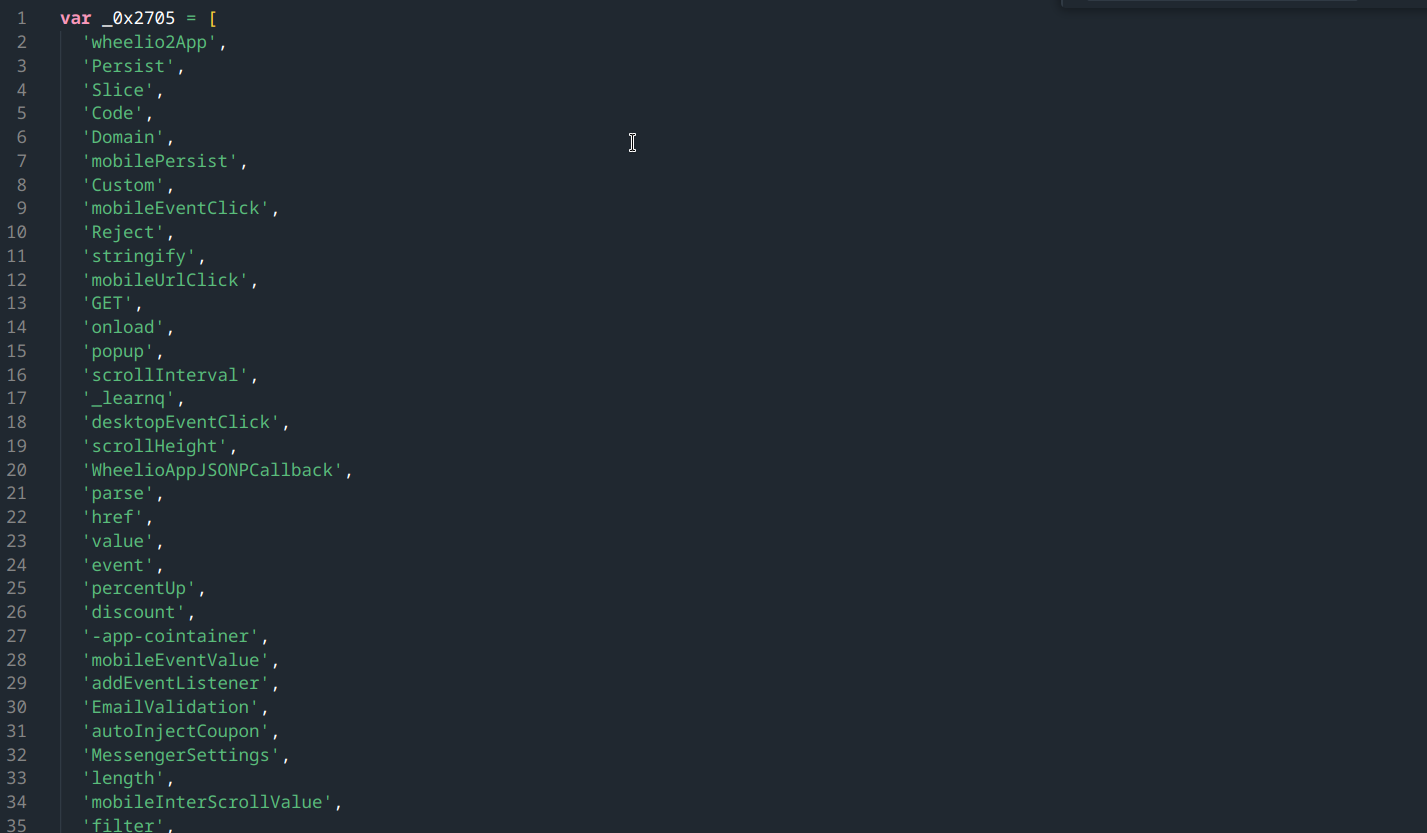
As I scrolled through the code, I didn’t find any discount codes directly, but I did find something that looked like it decrypts some options: 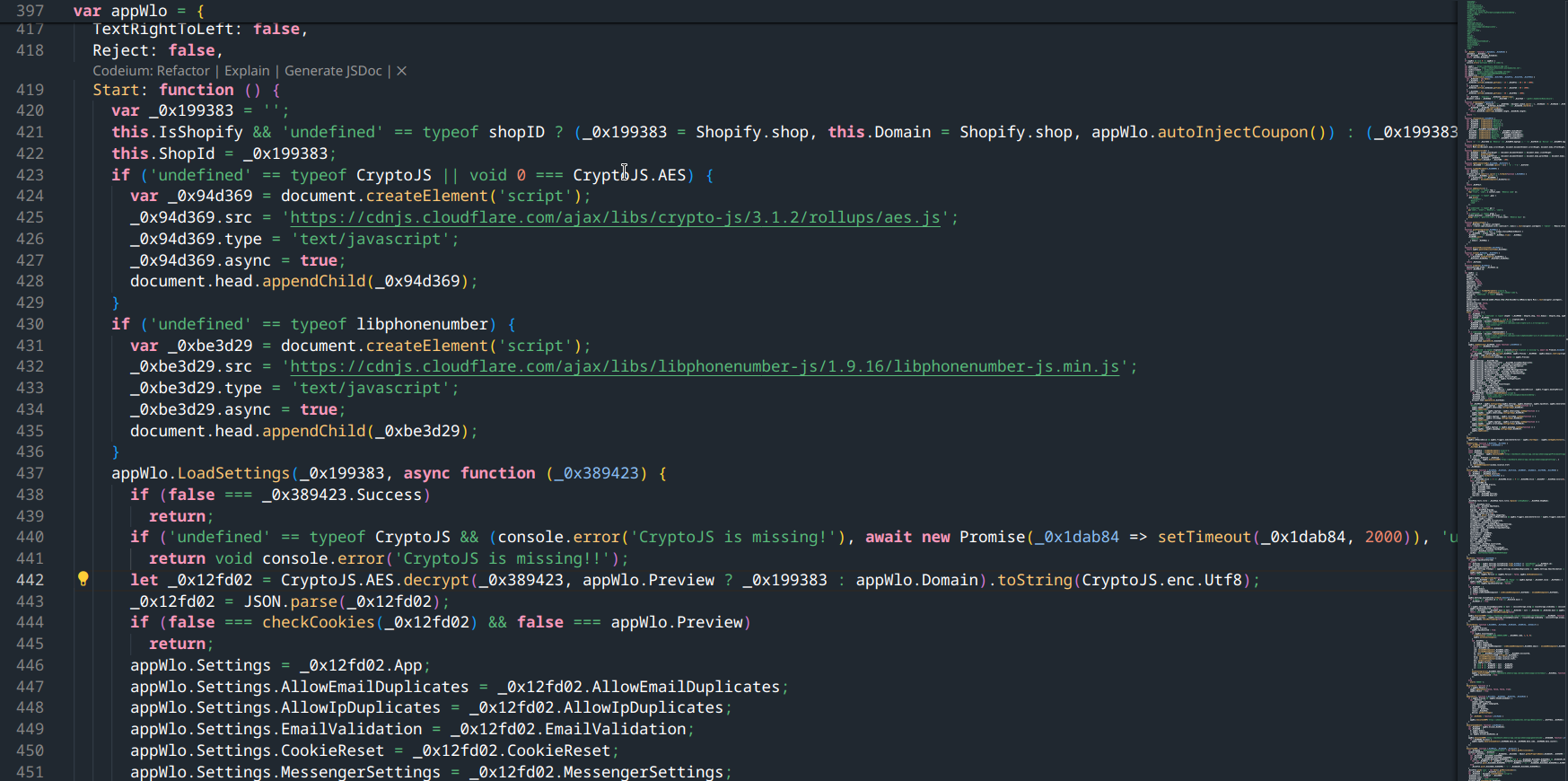
Then, I noticed in the browser console that it loads something from a URL that looks like this:
window['WheelioAppJSONPCallback261']('someAesStuff')
So, I pieced it all together and searched for the AES key, and acording to the code it's just the url (internally, they call it the ShopId, which you can get it by running console.log(appWlo.ShopId) in the browser console).
Decoding the Options
Now with the key and the AES-encrypted string, I wrote a few lines of javascript that mimics what the main script does.
// fill these values with your own
let encryptedData = "someAesStuff";
//let shopId = "e.g. myShittyDropshippingStore.myshopify.com";
let shopId = appWlo.ShopId;
// CryptoJS is also used by the official script to decrypt the data
let decryptedString = CryptoJS.AES.decrypt(encryptedData, shopId).toString(CryptoJS.enc.Utf8);
let parsedDecryptedSettings = JSON.parse(decryptedString);
console.log(parsedDecryptedSettings);
And after running the script, you'll see the decrypted settings in the console and discover just how rigged it is.
This is probably the worst "encryption" i've ever seen, as i think is only meant to keep out non technical users.
Update
And after all this work i found out that the easiest option is probably just running console.log(appWlo.Settings) in the Browser Console...
Update 2
I found out, another person already found out how they we're doing this. But now it's too late, and i'm still going to post this anyways. Turns out i'm not the only one that's cheap lol.